DIY: How to Verify LockChain QR Codes and Files Yourself using Bitcoin Blockchain Verification
- Greg Simon

- Jun 28, 2024
- 13 min read
Updated: Jun 28, 2024
LockChain is simply an interface to perform cryptographic functions that anybody can do. We value the core philosophies of Bitcoin which include self-sovereignty and decentralization. Therefore, your LockChain data is available to you always and we don’t want to be the only central entity that can perform these functions for you. So, in this blog I will show you how you, yourself can do all the verification functions that LockChain does. When I say LockChain data, I mean the following: If you enrolled, your public key and transaction ID are saved to your account and are accessible in the Profile section of the app. If you generated QR codes, your QR codes are always available to you on the app to regenerate and share or to simply access… even if you downgrade tiers or revert to the free plan. If you upload file hashes to the blockchain, the file hash and its transaction ID are also saved to your account and accessible in the Uploaded Data History fragment of the app.
Before we begin, I want to address a question you might have: If LockChain values self-control and sovereignty so much, how come we can’t perform the Bitcoin transactions ourselves? Indeed, we perform the Bitcoin transactions on our backend. But this was an easy decision to make for two main reasons. Firstly, by enabling Bitcoin transactions in the LockChain app, that would have opened an entire can of worms I was not comfortable with. If I were to have gone down this route, I would’ve had to get Money Transmitter Licenses for all the countries I wanted to operate in. This includes registering as a Money Services Business (MSB) with FINTRAC in Canada and FinCEN in the United States. Moreover, there are regulatory bodies who also deal with Know Your Customer (KYC) and Anti-Money Laundering (AML) laws such as The Proceeds of Crime (Money Laundering) and Terrorist Financing Act (PCMLTFA) in Canada and The Bank Secrecy Act (BSA) in the States. Consumer Protection Laws would also apply more stringently to LockChain if the app was a registered MSB. There are enough abbreviations from just these two countries alone to make anyone’s head spin, let alone a solo founder bootstrapping a startup.
The second reason pertains to simplicity and user-friendliness. We are not a Bitcoin company. Or more accurately, I don’t want to market it as one. While the Bitcoin layer is fundamental to our app, I want it to be as invisible to users as the TCP/IP or HTTPS protocols are when they browse this blog or website. Those base protocol layers are so foundational to the internet that I would approximate not even 10% of internet users know what it is or are aware of it, if even. That’s my goal with LockChain utilizing the Bitcoin network. I want the app to so seamlessly interact with the Bitcoin protocol that you don’t need to know how to use it or know what it is.
So, now that that’s out of the way let’s explore how you can use the data our app provides you to do your own verification using simple, free online tools. Before we begin, let’s quickly go over some terms so we are on the same page:
Transaction ID: A unique identifier for a Bitcoin transaction. We need these because the blockchain is huge. Each block can contain multiple transactions, resulting in over 1 billion transactions across more than 840,000 blocks. There are websites called “block explorers” that provide a user interface (as well as APIs which the app uses to query the blockchain) for you to search the ledger with. If you have your transaction ID, you can directly view the exact transaction that occurred.
Hash: There are many types of hashes in cryptography but in reference to LockChain, I am refering to SHA-256. Without getting too technical, a SHA-256 hashing algorithm essentially takes an input (example_input) and turns it into a fixed output (fjd2h39fj). This is a one-way function, meaning it’s impossible to turn fjd2h39fj back into example_input, but you will always get fjd2h39fj if you put in example_input. If even 1 piece of data in the file (input) changes, like an empty space or a capitalized letter, the output will be different. This is even true for videos and pictures in terms of frames and pixels. This globally used and established algorithm is basically a fool proof way of ensuring the original file was not tampered with.
Base64: Let's simplify what Base64 does. Imagine you have a book full of important information that you need to send across a network, but the network can only handle certain types of data efficiently. To make sure your book gets sent correctly and completely, you convert it into a special format that the network can easily manage and transmit without losing or altering any of the content. Base64 does exactly that – it converts your data into a format that is safe and efficient for transmission, ensuring it arrives exactly as intended.
OP_RETURN: In a Bitcoin transaction, OP_RETURN is a special field that allows you to embed up to 80 bytes of arbitrary data into the blockchain. This can be used for various purposes, such as storing a hash of a document or other important data. The data in the OP_RETURN field is not intended to be spent or used as part of a transaction but rather as a method of attaching metadata to a transaction in a way that is publicly verifiable and immutable.
Public Key: A public key is derived from a keypair. As you may know, Bitcoin wallets have a public address you can share with others to receive bitcoin, (a public key) and a seed phrase to send your bitcoin (private key). If someone gains access to your private key, they have access to your coins. Your keypair in terms of LockChain’s identity function is similar. If you lose access to your private key, then people can sign content and messages claiming to be you. This is why LockChain doesn’t provide the user their private key upon Enrollment. It is to protect the user from identity theft. Your private key is stored safely and securely on your device’s hardware security module which is isolated from the rest of your phone. Furthermore, our app hardcodes the enrollment process to ensure that only the user, after passing their phone’s verification, can access the private key for signing QR codes. Please note that if you uninstall the app or wipe your device, the private keys are also wiped. You will have to enroll again.
Okay, we can begin! Below are the free tools required to DIY LockChain functions. I found these with a quick google and there are tons of them online. You may find your own, but then you can’t really follow along with my screenshots. Also different sites will have different variables preset so you might get different outputs if you are not sure of the parameters to use.
Tools required:
Text to SHA-256 Generator: https://tools.keycdn.com/sha256-online-generator
Files to SHA-256 Generator: https://emn178.github.io/online-tools/sha256_checksum.html
Base64 Decoder: https://www.rapidtables.com/web/tools/base64-decode.html
Hex to PEM converter: https://holtstrom.com/michael/tools/hextopem.php
ECDSA Verifier: https://8gwifi.org/ecsignverify.jsp
Block Explorer: https://www.blockchain.com/explorer
Let’s start with file uploads.
File Uploads
When you have uploaded a file's hash to Bitcoin’s digital ledger using our app, you can view the data from it in the Uploaded Data History fragment of the app, which can be found on the Upload Data page. There, under the Begin Upload button you can find the files you have uploaded in the past. As you can see, the file name, date of upload and its digital fingerprint (the hash) is visible. If you tap on any of those files, the transaction ID is automatically copied to your clipboard.
Once you do that go to the block explorer. If you use a different explorer than what I listed, ensure that you are on a Bitcoin-specific explorer. Input the transaction ID.
Once your transaction is found, view the OP_RETURN field of the transaction. The format you will see is base64.
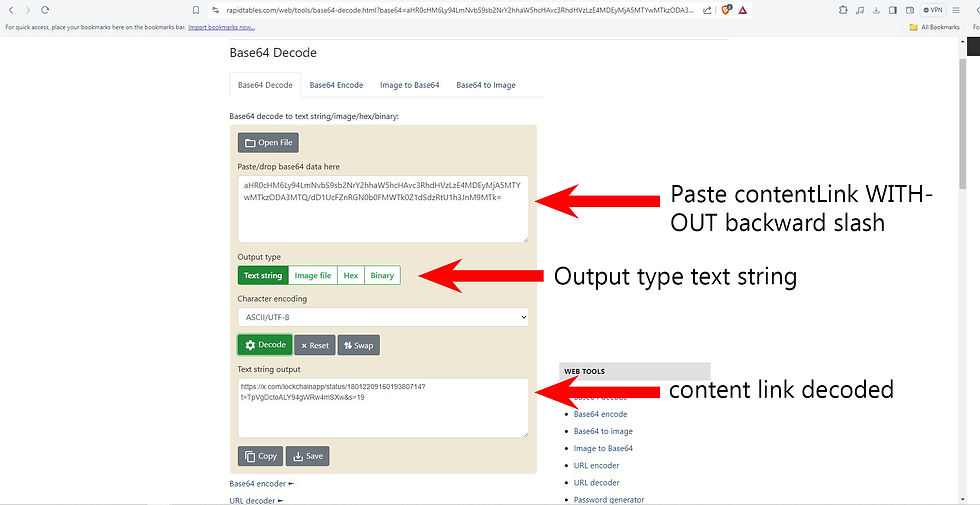
Go to the Base64 online tool and make sure your conversion is set to decoding Base64 -> hex. Paste the base64 formatted OP_RETURN from the explorer in the tool, and the hex output will be the file hash.
Now go back to the app and compare the hash of the file to the output you got from the online tool. That hash output will match what is on the blockchain if it is the exact original file.
You verified the file for yourself on your app, great. But what if I want to show others the file is tamper-proof? LockChain also offers that in the app. All you’d have to do is share the txID along with the file. You can even announce the txID in a tamper-proof QR code using our app for the highest-level of security. Your audience would then upload the file and input the txID. Our system hashes the file, and checks the blockchain using the txID to ensure that the file hash matches the blockchain hash. A match verifies that the file has not been tampered with at all.
Here’s how to do DIY:
The file in my screenshot is a pdf called “situationalawareness”, written by Leopold Aschenbrenner on the decade ahead in the field of AI. Wonderful read. You can find the pdf below or visit his website to download it yourself.
If Leopold wanted to prove to the world that pdf is the original file and has not be tampered with, then he would use our app to hash it, and upload that hash to the blockchain. For our DIY case, go to this free tool that converts files to SHA-256 hashes.
Upload his pdf to that tool and view the result of the hashing. Notice how the result is the exact same hash as the one that’s in my screenshots above. That means that I have downloaded the original, tamper-proof file from Leopold.
It seems like a lot of work just to verify a file. That’s why we have LockChain! The app does all of this within milliseconds for free on the Verify File fragment of the app. But the option for techies and cypherpunks to do it themselves will always be available.
Let’s move on.
Enrolled Identity:
Next, we will find your enrolled identity (public key) on the blockchain. Of course, you must be enrolled to do this. Once you have enrolled, head over to the Profile section of the app. There you will find the transaction ID and your public key.
Copy the transaction ID to clipboard and head over to the block explorer. Paste in the ID and view the transaction.
In the OP_RETURN section, you will find your public ID but this time, in hash format instead of base64.
Save that hash in a notepad. Next, copy the public key from your Profile.
Go to the SHA-256 converter tool online and paste in your public key and hit generate.
Take the hash that it generated, go to your notepad with the hash you got from the blockchain and paste it underneath. If it matches perfectly (caps included), you got yourself a match.
QR Code Verification:
Most modern smartphones have automatic QR code scanning capabilities, which means if you simply point your phone’s camera at a QR code it will scan it and provide you with a clickable link for you to visit. But there's no real link between a QR code and its creator. Phishing websites and imposters could scam audiences with fake content to lure them to their malicious QR code. This is why LockChain exists; to offer people an ability to verify that the QR code they scanned is linked cryptographically to the original, authentic user who generated it before interacting with it. That’s why our QR codes are more dense than regular ones; regular ones simply have a URL (website link) embedded in it, while ours has several types of data fields.
It is precisely this data in our codes that makes them the world’s most secure QR codes. Our team is constantly researching innovative solutions to try and compress the LockChain QR data, so the code is less dense and more legible without compromising security. When sharing LockChain QR codes, the user has to ensure the code is large enough for others to scan with their camera. But the most reliable way is the Upload QR Code function in the app, where you can upload a screenshot of a code. This method is much more reliable than scanning with the camera. Let’s explore the LockChain QR code verification process and how you can verify it yourself.
Let’s use the below QR code for example. To retrieve the QR code data from this code, simply scan it with your regular camera scanner.
Most smartphones will bring up some sort of notepad or text app to interpret the data. Open it up and observe the content. It should look something like this:
{"url":"{\"contentLink\":\"aHR0cHM6Ly94LmNvbS9sb2NrY2hhaW5hcHAvc3RhdHVzLzE4MDEyMjA5MTYwMTkzODA3MTQ/dD1UcFZnRGN0b0FMWTk0Z1dSdzRtU1h3JnM9MTk\\u003d\",\"publicKey\":\"3059301306072a8648ce3d020106082a8648ce3d0301070342000419f3d2fb15a364d6a556bf334fbf9337e7c6dde0753ae83635035eac7b37e91cef36128a8590b078cf170ea1d247f4c88c854a3ad6ae990eee363298b51c6b0e\",\"signature\":\"MEQCIDq/W1DIm1Y3cBX/cFo2wuafT4CTMfcdLMxJd/o44/FoAiAXv6uDuTzx+/xKR+JPCtLhob1G9DTE7djYNmbTXE4Qbw\\u003d\\u003d\",\"timestamp\":\"27/06/2024 15:59:02\",\"twitterUID\":\"\",\"txId\":\"7da340dec29e2d01043831ad61fb62a4a8a85e63455333c4a77cfbee26a5c5a1\"}"}If you look carefully, you will see the following data fields:
contentLink: This is the actual content that the original user who generated the code put in. Right now it is in base64 format.
publicKey: This is the public key of the user who originally generated the QR code. This identifies them and is on the blockchain for other users to verify.
signature: This is the signature that’s generated when the user signs their content with their private key. This is used to verify that the content wasn’t tampered with and that the public key belongs to the user who signed the content.
timestamp: This is the date and time the QR code was signed.
twitterUID: This is a special and public code unique to all twitter accounts. It is only included in QR codes if the user successfully logged into LockChain with Twitter and toggled to include their UID in the code.
txID: This is the transaction ID that points to the specific bitcoin transaction that has the user’s public key embedded into it. If the QR code is claimed by a twitter user, our code checks that the twitter UID and public key in the QR code matches the twitter UID and the public key stored in the user's account in the secure backend system of LockChain. Also, LockChain queries Bitcoin’s ledger using the txID to ensure that the public key used in the QR code is indeed recorded on the tamper-proof blockchain.
When copying the QR data from this JSON string, make sure to copy the data that is within the quotation marks ( " ) and leave the backward slash ( \ ) that comes before the closing quotation mark at the end. For example:
{"url":"{\"contentLink\":\"aHR0cHM6Ly94LmNvbS9sb2NrY2hhaW5hcHAvc3RhdHVzLzE4MDEyMjA5MTYwMTkzODA3MTQ/dD1UcFZnRGN0b0FMWTk0Z1dSdzRtU1h3JnM9MTk\\u003d\",\"publicKey\":\"3059301306072a8648ce3d020106082a8648ce3d0301070342000419f3d2fb15a364d6a556bf334fbf9337e7c6dde0753ae83635035eac7b37e91cef36128a8590b078cf170ea1d247f4c88c854a3ad6ae990eee363298b51c6b0e\",\"signature\":\"MEQCIDq/W1DIm1Y3cBX/cFo2wuafT4CTMfcdLMxJd/o44/FoAiAXv6uDuTzx+/xKR+JPCtLhob1G9DTE7djYNmbTXE4Qbw\\u003d\\u003d\",\"timestamp\":\"27/06/2024 15:59:02\",\"twitterUID\":\"\",\"txId\":\"7da340dec29e2d01043831ad61fb62a4a8a85e63455333c4a77cfbee26a5c5a1\"}"}Lastly, don't forget to unescape any fields of the QR data if need be:
replace \\u003d with =For example:
MEQCIDq/W1DIm1Y3cBX/cFo2wuafT4CTMfcdLMxJd/o44/FoAiAXv6uDuTzx+/xKR+JPCtLhob1G9DTE7djYNmbTXE4Qbw\\u003d\\u003dBecomes:
MEQCIDq/W1DIm1Y3cBX/cFo2wuafT4CTMfcdLMxJd/o44/FoAiAXv6uDuTzx+/xKR+JPCtLhob1G9DTE7djYNmbTXE4Qbw==
So, let’s start verifying each piece of data within the QR code. First, we will ensure that the content is valid and hasn’t been tampered with by performing cryptographic functions using online free tools. After we unescaped the contentLink, we input it into our base64 decoder. Do not include the backward slash after the = sign at the end.
Once the content link is decoded, you will see what the user originally put into the QR code. It can be any text; URL, address, coordinates, message, anything. In this case, it is a tweet link posted by LockChain. Let’s check that it hasn’t been tampered with and verify who generated this code. Take the public key from the QR code without the backslash and input it into the Hex to PEM converter tool:
Once you convert the public key to PEM format, head over to the ECDSA verification site. Follow the steps below to verify the content cryptographically.
First, you have to choose the proper parameter for the EC algorithm. This is “secp256r1”. Next we are looking to verify, not generate. So select the Verify Signature option. Third, you can ignore the private key portion as we are verifying and not generating. Next, paste the public key in PEM format from previously in between the begin and end sections of the public key, like so:
----BEGIN PUBLIC KEY----
MFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcDQgAEGfPS+xWjZNalVr8zT7+TN+fG3eB1Oug2NQNerHs
36RzvNhKKhZCweM8XDqHSR/TIjIVKOtaumQ7uNjKYtRxrDg==
----END PUBLIC KEY----
Next, you will paste the decoded content link (the URL of the tweet in plain text) into the message section. Lastly, paste the signature from the QR code content without the backslash after the == signs in the end into the signature section of the site. Click on “Submit”. If you pasted everything in correctly and the content truly hasn’t been tampered with, you will see the output signature with a green “Signature Verification Passed” message. If you want to see the power of this algorithm in action, go back to the plain text message and try changing the link. Delete or add characters, add an empty space, capitalize a letter… whatever tiny change you do, you will see the signature verification fail.
Okay, so now we know that the content in the QR code hasn’t been tampered with, great. But how do we know that the person who generated it is truly who they claim to be? Let’s verify the sender. If the user who generated the QR code didn’t include a twitter account link, then all we have is their public key. Users who choose this option most likely prefer privacy or want to announce their public key on their own terms, either on a different platform of their choice or to the people they choose. If your friend told you their public key, then you would write it down somewhere and know that it belongs to them. Any time they want to send you a QR code, you can verify the message is from them by checking the public key in the QR code.
If the user linked their Twitter account to LockChain, then a twitter UID will be found in the QR code. You can look up the user yourself with the twitter UID like this:
Replace $twitterUID with the actual twitter UID that is in the QR code. In the case of our example, it can be:
If you visit that link you will arrive to my personal twitter account.
Unfortunately, there is no way for you to 100% verify that a specific Twitter account generated the QR code. This is because LockChain performs this check on our secure backend servers. Our system parses through all LockChain user accounts on our backend servers looking for that specific Twitter UID. Since that Twitter UID is only saved to the LockChain user’s account if they successfully sign in using their Twitter credentials, a successful Twitter UID match will then proceed to check that the public key saved to the LockChain account is indeed the public key in the QR code along with the Twitter UID. This backend check confirms that the user who owns that Twitter account truly generated the tamper-proof QR code.

And there you have it. I hope that this DIY guide teaches you how our app performs these secure cryptographic functions in milliseconds, confirming the content and identities of users who generate QR codes. Public-private key cryptography has been around for decades. It truly revolutionized verification of messages between users. The only downfall was that to announce your public key to the world was to rely on third-party platforms or on peer-to-peer interactions. The former is subject to the control and liabilities of centralized platforms while the latter is not scalable. Now, with the advent of Bitcoin blockchain verification, we can use the world’s most distributed and secure ledger to announce to the world who we truly are, and to create the world’s most tamper-proof and secure content and QR codes. Protect yourself and your audience. Don’t trust. Verify.